Prepearing for GitHub certification - Manage GitHub Actions in the enterprise
Table of Contents
- Prepearing for GitHub certification - Manage GitHub Actions in the enterprise
Manage actions and workflows
Configure a GitHub Actions use policy
- GitHub Actions workflows contain actions
- Can create own action or use public ones
- Due to that is important to use policies for workflows and actions
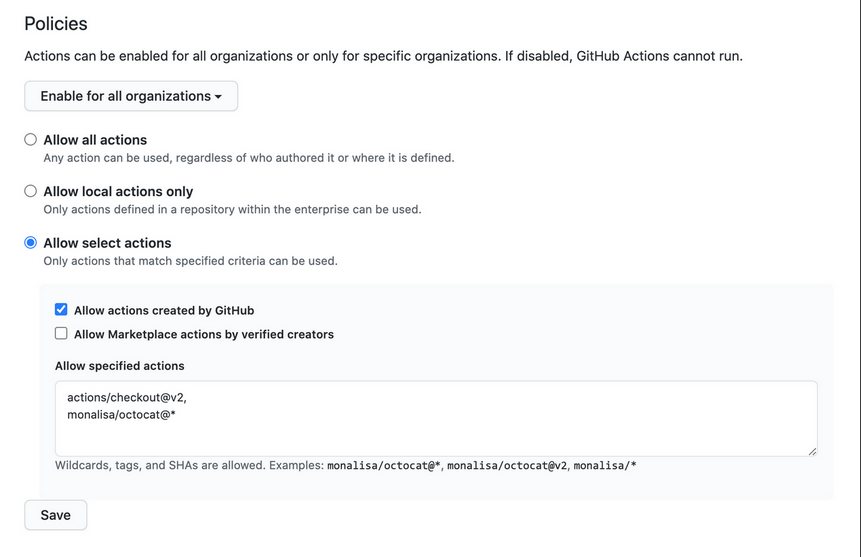
Action Policies
- Enable for all organizations - decided which organizations in your enterprise can use GitHub Actions
- Policies can be set on different levels
- allow all action
- allow local actions only
- allow select actions
- Artifacts and log retention
Manually sync public actions for Enterprise Server
- Official GitHub-Auhtored actions are bundled in Enterprise server
- Can configure which public actions can be used
NOTE:
- GitHub
actions-synctool: Possibility to manually download and sync actions into your enterprise instance
Document corporate standards
- Repositories for storage
- Files/folders naming conventions
- Location of shared components
- Plans for ongoing maintenance
- Contribution guidelines
Create workflow templates
- Supported in Enterpise Cloud and Enterpise Server
- Users need write access to an org
.githubrepository to create templates - Workflow templates can be used to creat new workflows in public and private repositories of the organization
- Need repository
.github-> and directoryworkflow-templates - Need a
ymlworkflow file - Need a json metadata file that describes how the template should be presented
NOTE:
-
The metadata file must have the same name as the workflow file. Instead of the .yml extension, it must be appended with .properties.json. For example, a file named octo-organization-ci.properties.json contains the metadata for the workflow file named octo-organization-ci.yml.
-
Sample workflow:
name: Octo Organization CI
on:
push:
branches: [ $default-branch ]
pull_request:
branches: [ $default-branch ]
jobs:
build:
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v2
- name: Run a one-line script
run: echo Hello from Octo Organization- Sample json file
{
"name": "Octo Organization Workflow",
"description": "Octo Organization CI workflow template.",
"iconName": "example-icon",
"categories": [
"Go"
],
"filePatterns": [
"package.json$",
"^Dockerfile",
".*\\.md$"
]
}Manage runners
Choose an appropriate runner for your workload
- NOTE: GitHub-hosted runners are only available for Enterprise Cloud. If you have an Enterprise Server instance
- GitHub-Hosted runners
- Are managed and maintained by GitHub
- Self-hosted runners
- Need to manage OS and Software
- You are responsible for maintaining it
Configure access to self-hosted runners
- Can create a Group of self-hosted runners to control access who can use it (either on Enterprise or Organization level).
- Runners can only be in one group at a time
Configure self-hosted runners for enterprise use
- Customize your self-hosted runner either with:
- Labels - Come in handy when you need to run jobs on runners that have specific capabilities.
- Proxy servers - communicate with GitHub via a proxy. Can be configured with
.envfile on server link - IP Allowlists
Monitor and troubleshoot self-hosted runners
The main steps you can take when troubleshooting a self-hosted runner are:
- Check the status of the runner in the GitHub Actions settings of the organization, repository, or enterprise where your self-hosted runner is registered (under Actions for an organization or repository, under Policies > Actions for an enterprise).
- Review the activities and automatic updates of the runner in the
Runner_files in the_diagfolder. - Review the status of the jobs the runner executed in the
Worker_files in the_diagfolder.
Manage encrypted secrets
Secrets
- Secrets are encrypted environment variables you can create to store tokens, credentials or any other type of sensitive information
- Available to use in the workflows and actions that have access to the organization, repository, or repository environment where they are stored
Access encrypted secrets within actions and workflows
-
{% highlight yml %} ${{ secrets.MY_SECRET }} {% endhighlight %}
- Access in yml
-
To access an encrypted secret in a workflow, you must use the context of the secret in your workflow file. For example:
{% highlight yml %} steps:
- name: Hello world action with: # Set the secret as an input super_secret: ${{ secrets.SuperSecret }} env: # Or as an environment variable super_secret: ${{ secrets.SuperSecret }} {% endhighlight %}
- Access in Action
- To access an encrypted secret in an action, you must specify the secret as an input parameter in the action.yml
inputs:
super_secret:
description: 'My secret token'
required: true