Prepearing for GitHub Administration certification - Introduction to GitHub Administration
Table of Contents
- Prepearing for GitHub Administration certification - Introduction to GitHub Administration
GitHub administrators work to ensure that their organization’s code and content assets are protected while providing each team access to the repositories they rely on to collaborate and share their work.
What is GitHub administration?
As a GitHub administrator, your goal is to keep everything working smoothly for your users
Administration at team level
- Each user is an organization member that can be added to a team
- You can create teams in your organization with cascading access permissions and mentions to reflect your company or group’s structure
- Teams are useful for
- Refining repository permissions
- Enabling communication and notification between team members
- Can sync teams with identiy provider groups
- eg: Azure AD - when syncing a GitHub team with Azure AD, changes to the Azure AD group are automatically reflected on GitHub, reducing the need for manual updates and custom scripts.
- Can use an Azure AD with team synchronization:
- Onboarding new members,
- granting new permissions for movements within an organization
- Removing member access from the organization
Members of a team with team maintainer or repository admin permissions can:
- Create a new team, as well as select or change the parent team.
- Delete or rename a team.
- Add / remove members from a team or sync GitHub teams with IdP group
- Add / remove outsside collaboratprs
- Enable or disable discussions
- Change visibility of the team within the org
- Manage automatic code review assignemts for PRs
Best practices for team-level administration
The following are some best practices for setting up teams on GitHub:
- Create nested teams to reflect your group or company’s hierarchy within your GitHub organization.
- Create teams based on interests or specific technology.
- Enable team synchronization between your identity provider (IdP) and GitHub.
Administration at organization level
In GitHub, organizations are shared spaces enabling users to collaborate across many projects at once. Owners and administrators can manage member access to the organization’s data and repositories with sophisticated security and administrative features.
Members of an organization with the owner permission at organization level can:
- Invite users to join the organization, as well as remove members from the organization.
- Organize users into a team, and grant “team maintainer” permissions to organization members.
- Add or remove outside collaborators to organizational repositories.
- Grant repository permission levels to members, and set the base (default) permission level for a given repository.
- Set up organization security.
- Set up billing or assign a billing manager for the organization.
- Extract various types of information about repositories via the use of custom scripts.
- Apply organization-wide changes such as migrations via the use of custom scripts.
The recommendation is to setup only one orgamization fro userts and repositories. If multiple organization are needed be aware:
- It is not possible to duplicate an organization or share configurations between two organizations.
- Depending on your software providers’ policies, there might incur extra costs if you need to install some applications in multiple organizations.
- Managing multiple organizations is generally more difficult!
Administration at enterprise level
Enterprise accounts include GitHub Enterprise Cloud and Enterprise Server instances and enable owners to centrally manage policy and billing for multiple organizations.
At the enterprise level, members of an enterprise with the owner permissions can:
- Enable SAML single sign-on for their enterprise account, allowing each enterprise member to link their external identity on your identity provider (IdP) to their existing GitHub account.
- Add or remove organizations from the enterprise.
- Set up billing or assign a billing manager for all organizations in the enterprise.
- Set up repository management policies, project board policies, team policies, and other security settings that apply to all the organizations, repositories, and members in the enterprise.
- Extract various types of information about organizations via the use of custom scripts.
- Apply enterprise-wide changes such as migrations via the use of custom scripts.
How does GitHub authentication work?
GitHub’s authentication options
Username and password
- Admins can allow users to continue using username and password authenticaiton method (also known as “basic” HTTP auth scheme)
- The recommendation is to use one of the other options below.
Personal access tokens
- Personal access tokens (PATs) is an alternative to using passwords to authenicate with GitHub when using the API or CLI.
- Token is generated via GitHubs settings option and tie the token permissions to repo or organization.
- Token can be used in the git command-line tool when username and password is asked for
SSH keys
- An alternative to using personal access tokens
- Users can connect and authenticate to remote servers and services via SSH with the help of SSH keys
- SSH keys eliminate the need for users to supply their username and personal access token for every interaction.
- Can be authorized to use with repo owened by an organization that uses SAML SSO.
- If org provides SSH cert, users can also use it to access repos without adding it to the GitHub account
Setting up SSH:
- Users generate an SSH key
- Add to ssh-agent and to GitHub Account
- Ssh-agent enusres an extra layer of security through the use of passpharse
- Users can config to use the local copy of git to automatically supply passharse or manually
Deploy Keys
- Another type of SSH keys in GitHub to grant access to single repo
- GitHub attaches the public part of the key directly to the repository
- Private part of the key remains on the user’s server
-
By default are
read-only, can give them write accessGitHub’s added security options
Multi-factor authentication
- MFA / 2FA - users need to provde an additioanl from of authenication to have access
- For GitHub the second form of auth is a code generated by an application on users mobile device or sent by Text message
- Users can only sign into their account if they know password and have access to auth code
- Organization owenres can require
- members
- outside collaborators
- billing managers to enable MFA
- Enterprise owners can also enforce certain security policies for all organizations owned by an enterprise account.
SAML SSO
- This type of authentication gives organization and enterprise owners on GitHub a way to control and secure access to organization resources like repositories, issues, and pull requests
- Organization owners can invite GitHub users to join their organization that uses SAML SSO - this allows users to contribute to the organization and retain their existing identity and contributions on GitHub
- GitHub will redirect them to the organization’s SAML IdP for authentication
- After successful auth, the IdP redirects to GitHub to access the organization’s resources.
Github offers limited support for all SAML 2.0 standards
- Active Directory Federation Services (AD FS)
- Azure Active Directory (Azure AD)
- Okta
- OneLogin
- PingOne
Lightweight directory access protocol (LDAP)
- Lets you authenticate GitHub Enterprise Server against your existing accounts and centrally manage repository access
-
GitHub Enterprise Server integrates with popular LDAP services like:
- Active Directory
- Oracle Directory Server Enterprise Edition
- OpenLDAP
- Open Directory
How does GitHub organization and permissions work?
Repository permission levels
-
As an organization member, each user is assigned a permission for a given repository
- Read - Recommended for non-code contributors who want to view or discuss your project
- Triage - Recommended for contributors who need to proactively manage issues and pull requests without write access.
- Write - Recommended for contributors who actively push to your project. This is the standard permission for most developers.
- Maintain - Recommended for project managers who need to manage the repository without access to sensitive or destructive actions
-
Admin - Recommended for people who need full access to the project, including sensitive and destructive actions like managing security or deleting a repository.
- Admin can give organization members, outside collaborators, and teams different levels of access to repositories owned by an organization
Team permission levels
- easy way to asssing repo permissions
- Members of a child team also inherit the permission settings of the parent team
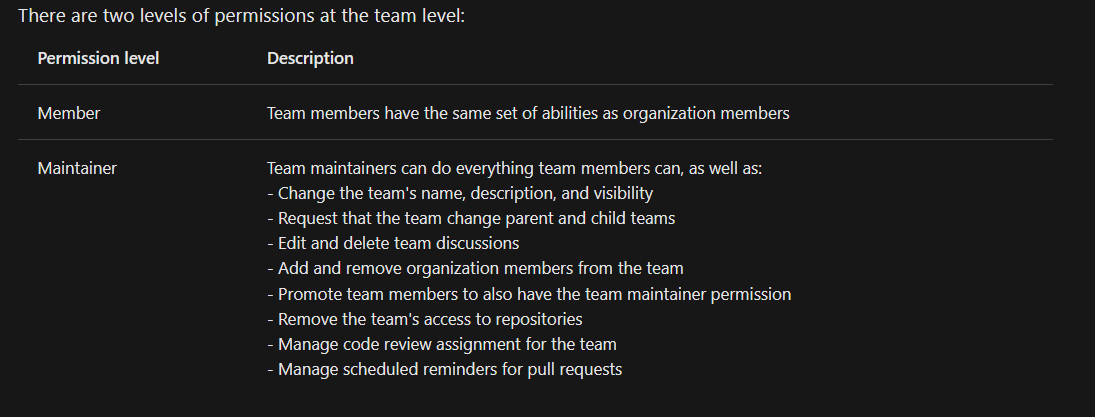
- To audit access to a repository view it in your settings
- TODO: Add image
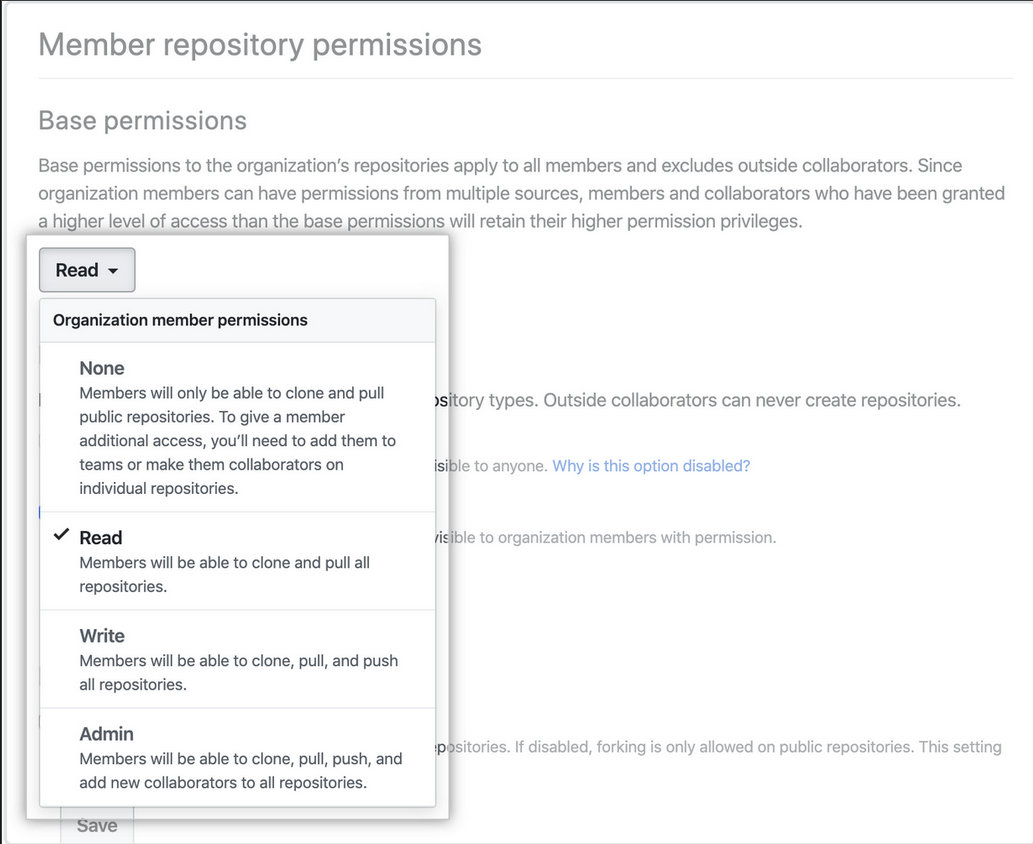
Organization permission levels
| Permission | Description |
|---|---|
| Owner | Can do everything organization members can, and can add or remove other users to and from the organization |
| Member | Can create and manage organization repositories and teams |
| Billing manager | Can only view and edit billing information |
Can also set default permissions for all members of your organization
Enterprise permission levels
- Enterprise accounts are collections of organizations
- Each individual user account that is a member of an organization is also a member of the enterprise
- Various settings related to authentication can be controlled from this higher level
There are three levels of permission at the enterprise leve
| Permission | Description |
|---|---|
| Owner | Have complete control over the enterprise and can take every action, including managing administrators, adding and removing organizations to and from the enterprise, managing enterprise settings, enforcing policies across organizations and managing billing settings |
| Member | Have the same set of abilities as organization members |
| Billing manager | Can only view and edit your enterprise’s billing information and add or remove other billing managers |
- Can also set a policy of default repo permission across your organizations

Note:
- Also consider giving default read permissions to all members of your organization/enterprise and adjusting their access to repositories on a case-by-case basis
- If its a small organization/enterpise you could also give all memebers write permission by default