- Prepearing for GitHub Advanced Security certification - Configure and use secret scanning in your GitHub repository
- Configure secret scanning
- Use secret scanning
- Excerice
Prepearing for GitHub Advanced Security certification - Configure and use secret scanning in your GitHub repository
What is secret scanning?
- Secrets are any authentication credentials
- If you commit a secret into a repository, anyone with read access to the repository can use it to access the external service with your privileges.
- GitHub Advanced Security feature that scans repositories for known types of secrets
How does secret scanning work?
- Secret scanning automatically scans your entire Git history on all branches present in your GitHub repository for any secrets.
- When a secret with a known pattern is committed into a private or public repository in your project, notification is sent to admins of the repository.
- Administrators can then view the list of all detected secrets in the Security tab.
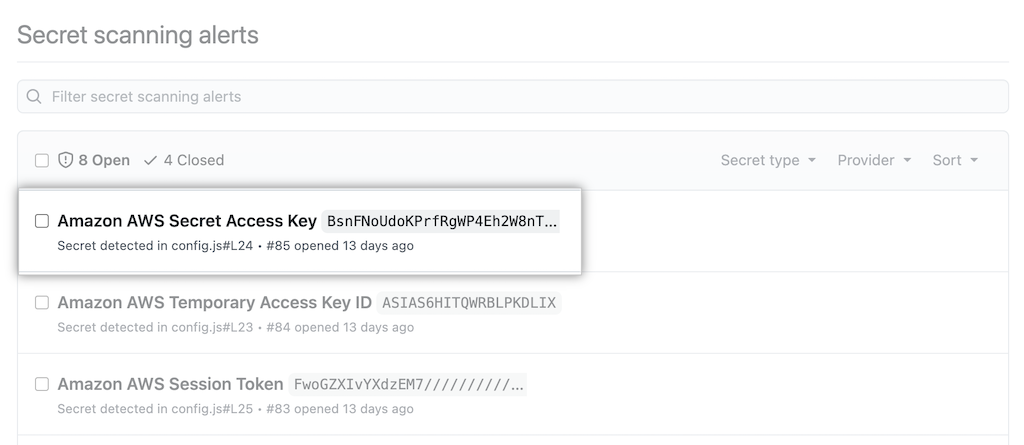
- GitHub also notifies the service provider who issued the secret.
- The service provider can then take any appropriate action
- Revoking secert
- issuing a new secret
- reaching out to you direcrtly
- etc..
For a list of the service providers and patterns automatically detected by GitHub in public and private repositories, please check out About secret scanning.
Organizations using GitHub Enterprise Cloud with GitHub Advanced Security can run secret scanning on private repositories. For more information, see the GitHub Enterprise Cloud documentation.
If you cannot see the secrets used in you organization you can create a custom pattern for them.
Who is secret scanning available to?
- Available for all public repositories
- Private repositories owned by organizations on an enterprise plan where GitHub Advanced Security is enabled.
Note:
- Secret scanning is enabled by default on public repositories and cannot be configured or turned off. It can only be turned off for private repsitories with GHAS.
- Secret scanning must be enabled manually on private repositories.
Configure secret scanning
- For private repos with GHAS you can configure secret scanning:
- Exlude files
- configure notification recipients
Enable secret scanning for a private repository
Enable secret scanning on a private repository:
- In your repository, navigate to Settings > Security & analysis.
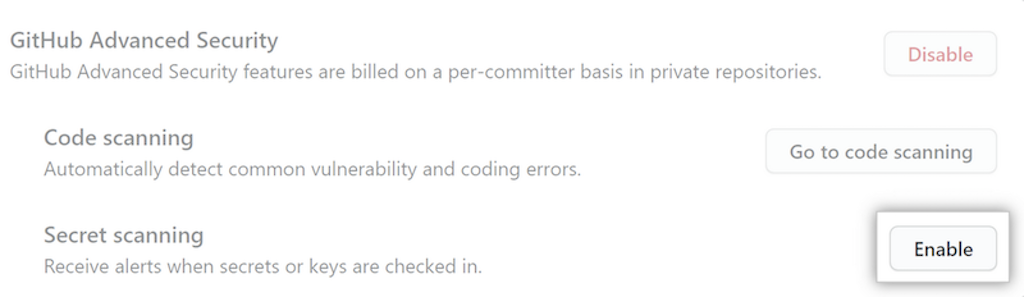
- Under Configure security and analysis features, click the Enable button next to GitHub Advanced Security.
- Review the impact of enabling Advanced Security and click Enable GitHub Advanced Security for this repository.
- Click the Enable button next to Secret scanning. If you see a Disable button, it means that secret scanning was * already enabled at organization level.
Enable secret scanning for an organization
Enabling secret scanning at organization level ensures that secret scanning is enabled by default on all private repositories where GitHub Advanced Security is enabled.
Enable secret scanning for an organization:
- In your organization, navigate to Settings > Security & analysis.
- Under Configure security and analysis features, click the Enable all button next to GitHub Advanced Security.
- Review the impact of enabling Advanced Security on all repositories and click Enable all.
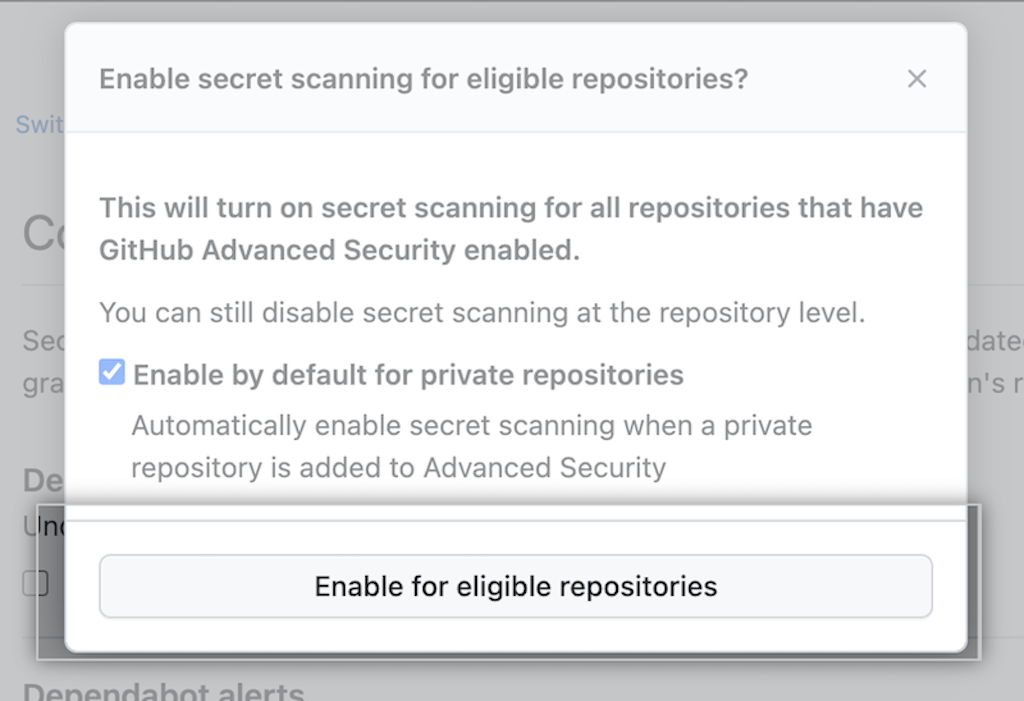
- Click the Enable all button next to Secret scanning.
- Optionally enable the feature by default for new repositories in your organization, and click Enable for * eligible repositories.
Exclude files from being scanned
- You can create a
.github/secret_scanning.yml - In the file, use
paths-ignore - can use
*to filter paths and more special characters.
paths-ignore:
- "foo/bar/*.js"Note:
- If there are more than 1,000 entries in paths-ignore, secret scanning will only exclude the first 1,000 directories from scans.
- If secret_scanning.yml is larger than 1 MB, secret scanning will ignore the entire file.
- Pattern cheat-sheet: https://docs.github.com/en/actions/using-workflows/workflow-syntax-for-github-actions#filter-pattern-cheat-sheet
Configure recipients of secret scanning alerts
- Applicable only if users are watching the repository and security notifications are enabled.
- Github notifies following users:
- Repo admins
- Organization owners
- Authors of commits that trigger alerts
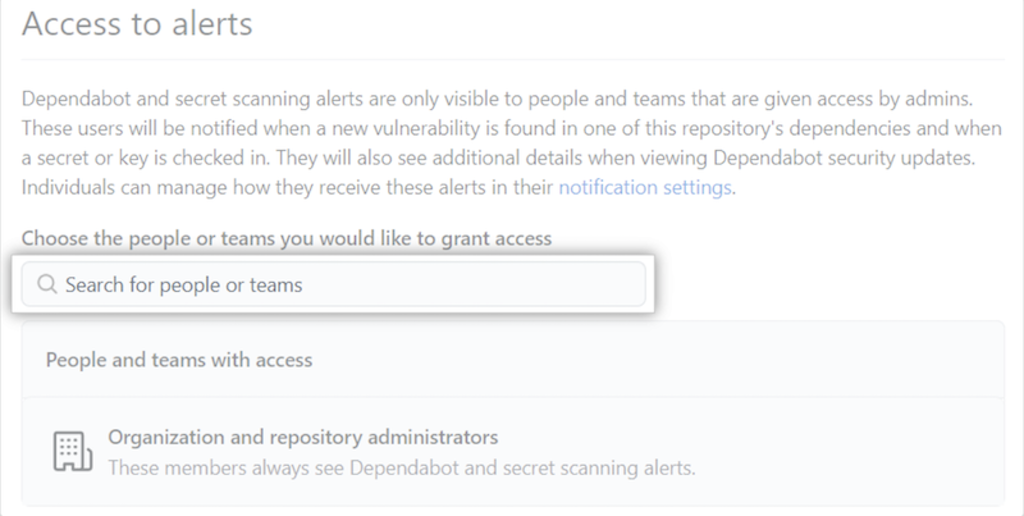
Also repo admins and org owners can provide access to security alerts to people or teams who have write access to the repository under Settings > Security and analysis.
Use secret scanning
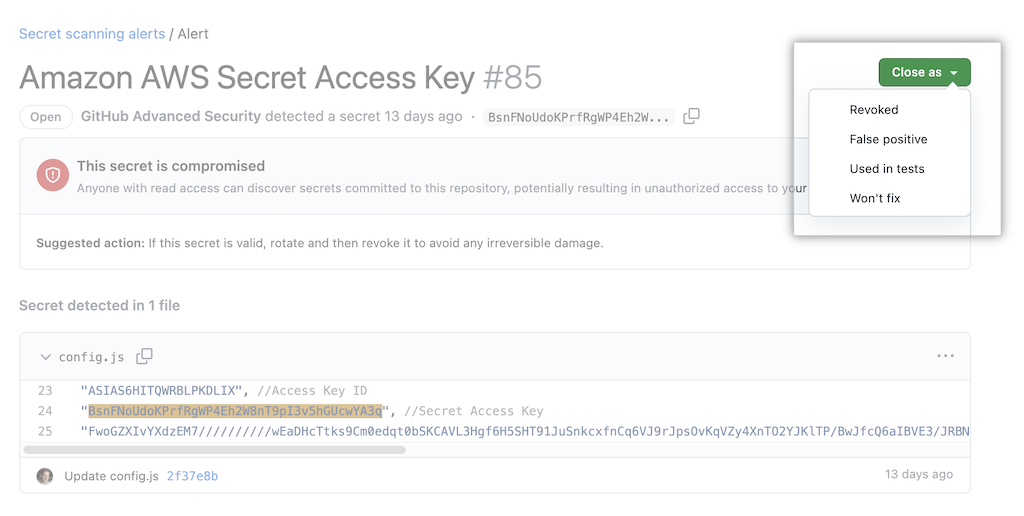
Respond to an alert
- Once commitet to repo, consider the secret comprimised.
- Recommended actions:
- Compromised GitHub personal access token, delete the compromised token, create a new token, and update any services that use the old token.
- All other secrets, first verify that the secret committed to GitHub is valid. If so, create a new secret, update any services that use the old secret, and then delete the old secret.
- Once actions has been taken, you can resolve the alert under Security > Secret scanning alerts by choosing a reason in the Close as dropdown
Create a custom pattern
- You can define up to 500 custom patterns for each organization or enterprise account, and up to 100 custom patterns per private repository.
For a private repository
Create a custom pattern for a private repository:
- In your repository, navigate to Settings > Security & analysis.
- Under GitHub Advanced Security > Secret scanning, click New pattern.
- Provide the following details for your custom pattern:
- The name of the pattern
- The pattern of the secret specified as Hyperscan regex
- A sample test string to make sure your configuration is matching the patterns you expect
- Also can add more options under More Options drowpdown.
For an organization
Create a custom pattern for an organization :
- In your Organization, navigate to Settings > Security & analysis.
- Under GitHub Advanced Security > Secret scanning, click New pattern.
- Provide the following details for your custom pattern:
- The name of the pattern
- The pattern of the secret specified as Hyperscan regex
- A sample test string to make sure your configuration is matching the patterns you expect
- Also can add more options under More Options drowpdown.
Excerice
Good excerice to put the knowledge you have learned to use here